Passwords are the primary way we protect our online accounts from unauthorized access. However, passwords themselves can be vulnerable to attacks. One of the most effective ways to secure passwords is through hashing, a technique that converts a password into a unique string of characters that cannot be reversed.
In this article, we will explore the concept of hashed passwords, including how they work, why they are important, and how they are used in practice.
What are Hashed Passwords?
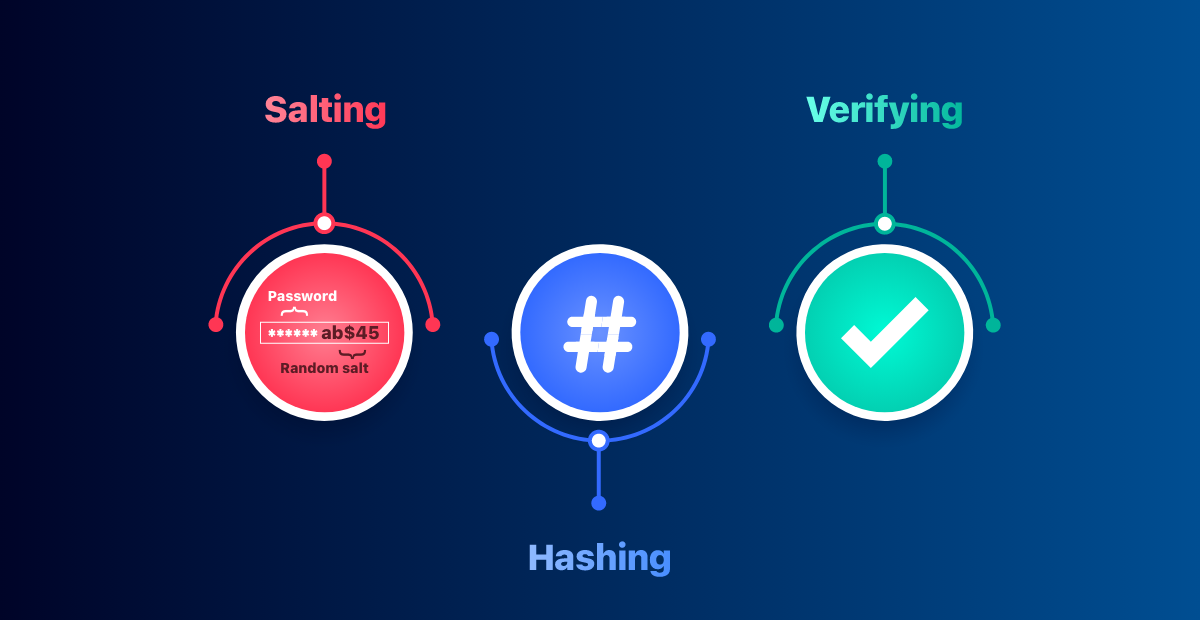
A hashed password is a password that has been converted into a unique string of characters using a mathematical algorithm. When a user creates a password, the password is passed through a hashing function, which produces a fixed-length string of characters known as a hash. The resulting hash is then stored in a database instead of the original password.
When a user attempts to log in to their account, the password they enter is again hashed using the same algorithm, and the resulting hash is compared to the hash stored in the database. If the two hashes match, the user is granted access.
Why are Hashed Passwords Important?
Hashed passwords are important because they provide an additional layer of security to online accounts. Even if an attacker gains access to the database of hashed passwords, they would not be able to determine the original passwords without knowing the hashing algorithm and the salt value used to generate the hashes.
In addition, hashed passwords can protect against attacks that rely on password reuse. Many people use the same password for multiple accounts, which can lead to a domino effect if one account is compromised. By hashing passwords, even if an attacker gains access to one account’s password, they would not be able to use it to access other accounts that use the same password.
How are Hashed Passwords Used in Practice?
Hashed passwords are used in a variety of ways in practice, depending on the specific application or system. However, there are some common techniques and best practices that are used across many applications and systems.
One common technique is to use a cryptographic hash function, such as SHA-256 or bcrypt, to generate the hash. These functions are designed to be secure and resistant to attacks.
Another best practice is to use a salt value when generating the hash. A salt is a random string of characters that is added to the password before it is hashed. This helps to prevent attacks that use precomputed hash tables, which are databases of precomputed hashes for commonly used passwords.
Code Example:
Here’s an example of how to hash a password using Python’s hashlib library:
import hashlib
password = "mypassword123"
# Generate a salt value
salt = os.urandom(16)
# Combine the password and salt
salted_password = password.encode('utf-8') + salt
# Hash the salted password
hash = hashlib.sha256(salted_password).hexdigest()
Frequently Asked Questions:
Q: Can hashed passwords be decrypted?
A: No, hashed passwords cannot be decrypted. Hashing is a one-way process that cannot be reversed. However, an attacker could use a technique called a brute-force attack to guess the original password by trying many different possible passwords until they find a match.
Q: How do I know if my passwords are hashed?
A: If a website or application stores passwords securely, they will almost always use some form of hashing. However, there is no way to know for sure without access to the system’s source code or documentation.
Q: What is a salt value?
A: A salt value is a random string of characters that is added to a password before it is hashed. The salt value helps to prevent attacks that use precomputed hash tables.
Conclusion:
Hashed passwords are an important part of modern online security. By converting passwords into unique strings of characters that cannot be reversed, hashed passwords provide an additional layer of protection against unauthorized access. While there is no guarantee that a system that uses hashed passwords is completely secure, using a strong hashing algorithm and salt value can greatly increase the difficulty of attacking the system.
Overall, hashed passwords are an essential tool for protecting online accounts and ensuring the security of sensitive information. As technology continues to evolve, it is likely that new techniques and best practices for hashing passwords will emerge, and it is important to stay up-to-date on the latest developments in this area.
